IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 23 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 14 countries to choose from, rental period from 2 days.
Resident
From $0.90 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
A forward proxy server, or more descriptively, a client-side intermediary server, is a gateway that services requests from the user, sends them to the required resource, and sends back the answer. It assists in concealing the actual IP address, controlling outbound traffic, circumventing geo-blocks, and is often employed for data scraping, business filtering, or viewing otherwise unavailable information.
This article will examine the best forward proxy features, discussing the most notable advantages and the most prevalent areas of application.
Such a server, as already mentioned, sits in the middle of a network as an additional layer that obscures where the request originated from. This is how it operates step-by-step:
Some examples of the most relevant considerations for such routing systems would be IP rotation, session control, caching, filtering of traffic, control of access, logging, and auditing. Logging is usually done on a provider basis and captures traffic in and out of the network with recorded errors, debug, analyze session statistics, and traffic sessions monitored. In case you need a rotation option you'll need dynamic rotating proxies.
The primary difference stems from which IP address is obscured. A forward server is client side-based, therefore it is programmed to blanket the user’s IP address. Most commonly, they are used to bypass restrictions, manage multiple accounts, or automate browsing tasks.
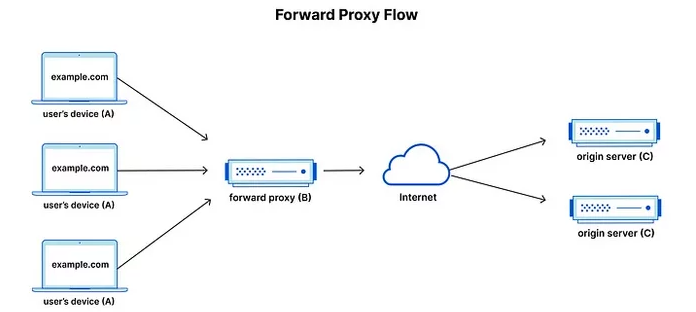
The opposite is true for a reverse proxy as they sit on the server side concealing the IP address of the originating server. Its main tasks are load balancing, security filtering, and inbound traffic distribution.
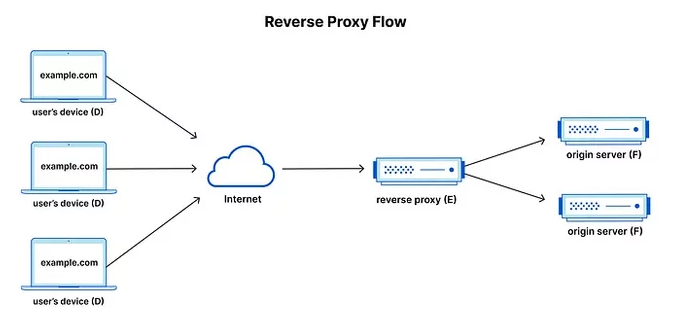
Reverse proxy tend to be more specialized compared to forward ones. Examples include WAFs (Web Application Firewalls), Load Balancers, TLS Termination Proxies, and API Gateways. Whereas forward proxy servers are primarily used for anonymity and access routing. Thus, both types are suitable for entirely different use cases.
Forward proxy server solutions could be organized by the type of protocol used (HTTP/HTTPS/SOCKS5) or by type of IP (datacenter, residential, mobile, ISP). This affects how and where they can be used.
This tool is frequently utilized to provide employees access to, or limit their access to, certain portals or websites. It monitors outgoing requests and applies rules for blocking content or allowing access only to business-related resources. This form of supervision minimizes data leaks, improves productivity, and enhances monitoring.
When a user accesses a particular website or downloads a file for the first time, a copy is saved on the server. Data can then be retrieved from the cache rather than the origin host on subsequent visits, thereby lowering bandwidth consumption and improving access speed.
The user’s IP address is hidden, allowing anonymity and privacy while simultaneously enabling numerous other advantages: protecting users from geo-blocks and sensitive data restrictions, preventing bans or rate limits – especially for multi-account management or bulk action tasks.
Scraping the web is one of the most popular data gathering activities that people undertake. Data scraping can be done manually, but it is much easier to automate using a software application. One of the most powerful tools for scraping is bots. These bots are capable of handling numerous IP addresses, which makes the process easier. With the help of such bots and forward proxy software, one can bypass any limitations for sending requests etc.
Achieving success in this area requires proper implementation of a strategy: steering IPs through residential or mobile proxies, rotating IP pools, customizing headers, managing requests intervals, and other practices minimizes CAPTCHA and blacklisting exposure.
Such servers can enable the access of platforms that have not been made available in some geographies. Users masquerade as guests from other countries or cities by altering the origin of the request's true geographic location. Such methods are routinely implemented to bypass state censorship or corporate firewalls.
Having explained how this type of server works, as well as its benefits, let us now look at the options available for setting up a forward one of your own. Below are the best software tools and services for configuration that can assist you in setting up a custom network routing framework.
As noted, these solutions are best suited for proprietary company use because of the essential requirement for detailed control, centralized traffic analysis, access control logging, and filtering capabilities for optimal infrastructure and security policy compliance.
The Squid project provides a variety of software solutions for managing intermediary servers and is an exceptionally versatile intermediary system manager. Client-side applications like web browsers or desktop messengers connect to Squid in forward mode. Then Squid sends their queries to external servers.
Configuration is handled via a dedicated settings file located at: /etc/squid/squid.conf или /usr/local/squid/etc/squid.conf.
By defining the host and port parameters in Squid, you can:
Moreover, user authentication can be integrated if further expansion is needed in the Squid configuration.

This utility is an attractive alternative for small scale setups and personal computers. With support for HTTP, HTTPS, and SOCKS4/5, this tool is very versatile.
Simulating natural browsing behavior, all configuration is done through the 3proxy.cfg file in which you set up hostnames, ports, logins, and timeouts.
Unlike other solutions, this one allows different types of intermediaries to be simultaneously used. For example, you can enable HTTPS and SOCKS5 modes at the same time. Access control is provided through allow, deny, and auth directives enabling restrictions based on IP or user permissions. Caching and logging are also supported alongside these enabling environments with many users or departments to share resources.

TinyProxy is an HTTP/HTTPS tool specifically developed for non-demanding systems. It allows clients to redirect traffic while hiding the user’s true IP address.
The configuration is managed via the /etc/tinyproxy/tinyproxy.conf file, where the administrator specifies the server host and port.
More advanced alternatives can use authentication but with this option, user authentication is not provided readily, meaning additional setup with patches is required.

Although primarily designed to function as a reverse one, NGINX is also capable of operating as a forward proxy server after some modification to its modules and directives for handling HTTP/HTTPS traffic, access control, activity logging, and connection security. NGINX is not as commonly used as a forward intermediary given the intricacy of the configuration, however, it is still a reasonable choice for seasoned administrators who need more granular control.
To sum up, we’ve covered the main software used to deploy a self-hosted forward proxy server. However, it’s important to note that improper configuration of such a system can introduce certain risks, in the next block we are going to look at them.
For the case of deploying the type of intermediary server described above, it is very crucial to choose the software very carefully. It is important to use the trusted solutions stated above to guarantee stable operation. However, some risks may be encountered while navigating through such a system. Let us take a deeper look at these risks below.
All these factors should be considered for the selection and setup of forward proxy servers. Additionally, consideration should be paid towards the provider’s role as a stakeholder. For instance, if the provider’s offered solutions come with pre-fitted security provisions like authentication, IP filtering, and monitoring tools, then these aid greatly in mitigating risks pertaining to security breaches and unauthorized access. Here, the provider is able to cover partial responsibility for baseline security while the user is able to sustain a robust and reliable system for traffic control.
A variety of commercial forward routing services offered by well-known providers exist alongside the option of configuring a server using dedicated software. These services are more user-friendly and accessible for non-expert users who are looking to bypass region restrictions on certain sites or have more guarantees of smooth social media interactions. The same applies to advanced users with more complex needs such as scraping, multi-account usage, automation, and software testing.
For users who want to set up a forward intermediary on their device quickly, we have provided comprehensive guides tailored to specific operating systems or applications:
These instructions enable users to create an effective and reliable connection through a forward server without the need for elaborate manual configurations.
Like their more secure counterparts, reverse proxies tend to be less popular, forward proxies still remain very relevant and widely used solutions when modern security measures are integrated. These tools, if configured correctly, provide a strategic balance between anonymity, access control, and traffic control whether in a corporate environment or in testing cases. When using forward routing tools, to attain this level of security and performance, a VPN, HTTPS, or SOCKS5 protocol needs to be implemented. These tools need to always have username/password security enabled to guarantee safety.
Setting up a server is optimal for IT professionals and businesses that require complete control over configuration details like security and traffic monitoring, whether for purposes of development, corporate networking, or data protection. On the other hand, marketers or freelance professionals who seek an uncomplicated and quick solution for altering their IP address to access geo-restricted content prefer using pre-packaged commercial systems.
