IPv4
From $0.70 for 1 pc. 40 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 40 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 40 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 21 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 14 countries to choose from, rental period from 2 days.
Resident
From $0.90 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
Proxy technologies enable users on macOS to engage with brands and resources online more securely and privately. They serve both personal and corporate purposes, for instance, accessing regionally restricted content or extending capabilities by altering the virtual location. Properly configured proxies enable effective network connection management on macOS while reducing exposure to data leaks or surveillance. This article will outline the specifics of operation and provide a comprehensive guide on macOS proxy settings, including type selection.
Such servers function as gateways between the user’s device and the world wide web. They steer network traffic through themselves, changing or disguising surveillance exposure data. Users can leverage them to achieve:
MacOS proxy settings grant users additional control options, offering more flexibility while safeguarding online activities.
When planning to perform macOS setup proxy, protocol type needs to be established first. Here are some of the most popular ones:
Indeed, protocols allow users to bypass certain restrictions while observing regional limits set by certain services. They can unlock other websites or alter parameters including the region.
Let's go through some of the steps necessary in configuring the system:
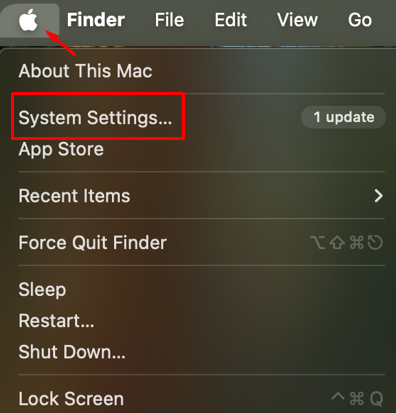
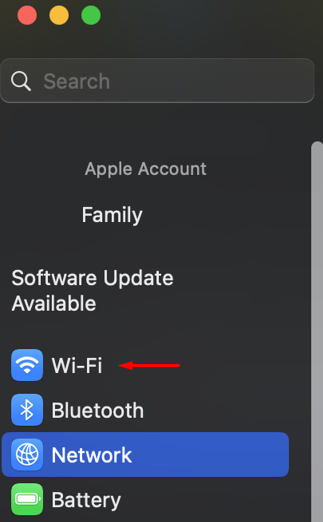
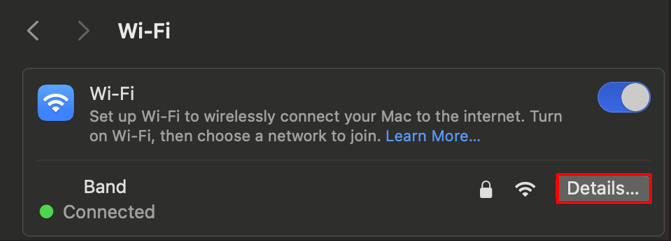
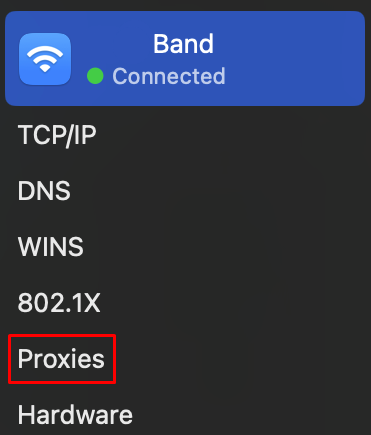
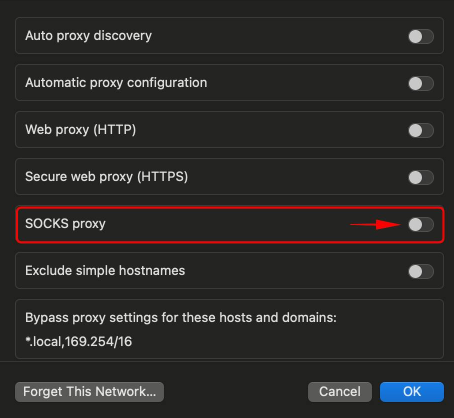
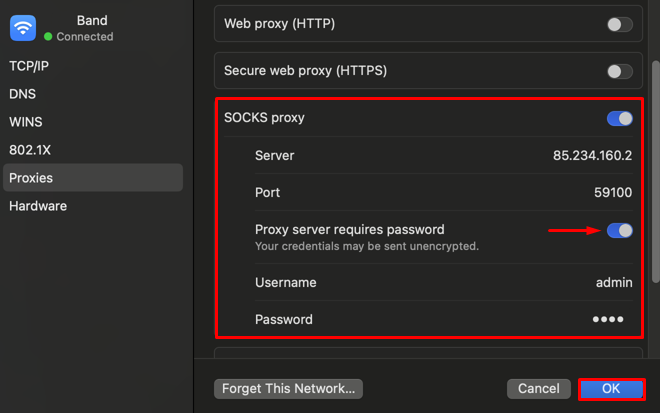
After macOS proxy settings your system will operate through the new IP address, including all programs and applications on the device.
You can check proxy settings on macOS by navigating to system parameters as mentioned above through active Wi-Fi connection. All previously set parameters will be displayed including type of server, IP address, port, and authorization details.
To verify if the macOS proxy settings are correct, a dedicated online checker is recommended. This, without a doubt, provides the fastest and most efficient answer without any further installations. To gain access, simply go to the tool’s webpage and you will receive the required details instantly.
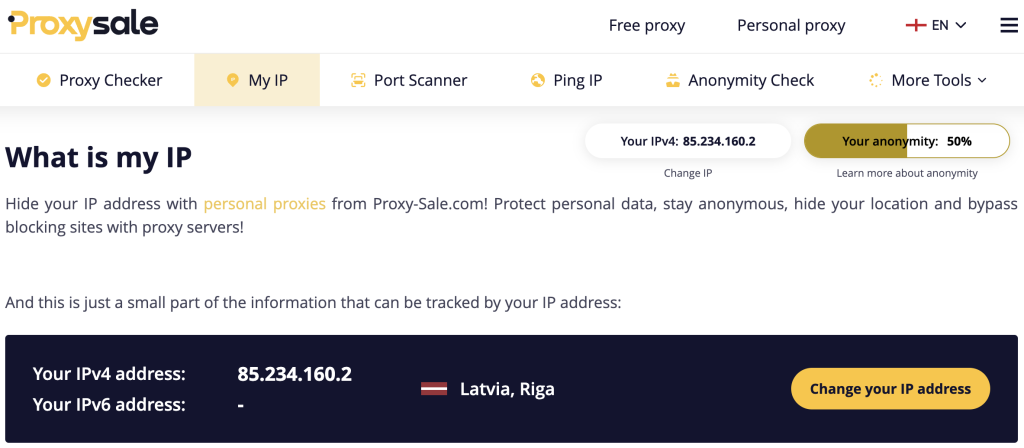
Such services enable determination of the external IP address within seconds and checking if a change happened as a result of performed actions. If the IP address correlates to the one stated in the settings, then the connection is successfully redirected through the designated waypoint.
For additional steps on how to monitor the IP address, utilize network diagnostics: for example, how to trace IP tools, which enables identification of potential speed problems within data transmission or routing problems.
In certain scenarios, the configured server may need to have some sites or domains excluded to ensure that the server does not actively work with those domains. This is the case if the resource does not function correctly through the proxy or needs direct connection through it without using an IP shift.
The field can be found immediately below the lines used for authorization input. Here, you are able to manually list the resources which you would want the activity to be excluded from. Enter them in the “Bypass proxy settings for these hosts and domains” field and separate them with a comma.
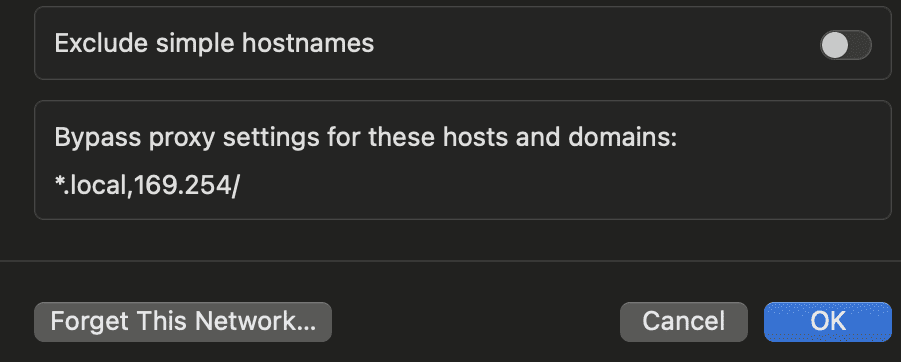
Hence, the system will automatically set the direction of traffic to those resources ensuring stable operations without interference from the configured server.
There are apps that for one reason or another make local macOS proxy settings. This is because it may create problems with navigation through the designated server for them. In such situations special tools can be of use – those are specialized applications which let you choose for which applications the traffic will be IP-channeled regardless of system settings.
The main benefits of such tools are as follows:
Proxifier is one of the best-known and trusted tools for macOS. This application is also useful for managing messengers, games, and business applications.
When using macOS and configure proxy, several issues arise that compromise connection quality. Let us discuss some major issues in detail.
Is characterized by Wi-Fi failing completely. In this scenario, some recommendations include:
As noted by slow loading of the pages in the browser and the applications, is a problem facing many users today. In many instances, the problem is caused by the slow speeds of the intermediary server or general congestion in the network.
In the case where the trustworthy private IP addresses with minimum delay possible are selected, and useless background tasks are disabled, the situation can be remedied.
Public and free options should strongly be avoided for macOS proxy settings. The reason being, these settings and configurations are usually set-up and leveraged by multiple users, which makes them predictable and, thus, subject to being used maliciously.
These problems arise when certain applications refrain from using the system defaults. In these cases, try to see if there is a manual server configuration option available in the application.
Examine also whether you have a VPN or its extensions within the browser turned on, and when using a “Proxifier” make sure that it actually forwards the traffic for the selected programs.
Purchase fast and quality servers from reputable companies. In addition, monitor the ping time to those IPs often to improve overall performance.
To summarize, configured macOS proxy settings offer an unparalleled method to maintain privacy, circumvent geo-restrictions, and optimize network connection. Proper configuration provides a means to control and protect personal information network traffic.
General recommendations:
Indeed, by following these recommendations, you will be able to avoid common problems and configure network processes without risking confidentiality loss.
