IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 23 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 14 countries to choose from, rental period from 2 days.
Resident
From $0.90 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
Every operating system has its vulnerabilities, and Linux is no exception. To ensure security and anonymity on the network, we recommend setting up a proxy. With proxy servers for Linux you will be able to:
If you already have a reliable personal proxy, let's move on to setting it up. We'll show you how to set a proxy through the command line using environment variables.
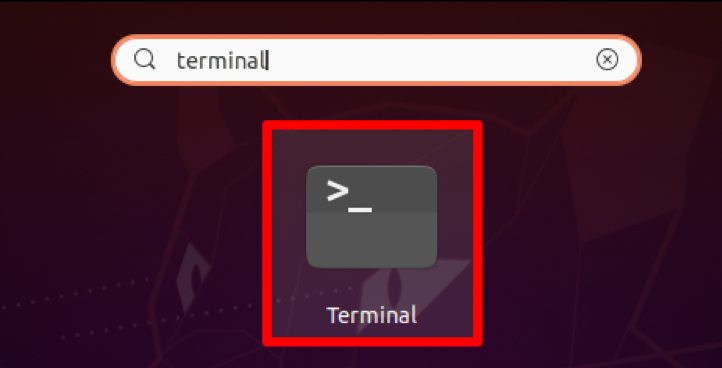
You can enter several proxies of different types at once (HTTP, HTTPS, SOCKS, or FTP) or select one type.
The proxy configuration is completed! This setup is suitable for any Linux-based operating system. This will help protect your data and device, and you will always remain anonymous online.
