IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 24 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 14 countries to choose from, rental period from 2 days.
Resident
From $0.90 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
Mobile proxy servers have an important role, acting as a bridge between a user’s device and the web. They conceal an original IP address and give access to web resources that are trying to be accessed from a specific region. However, correct settings must be defined in order to reap the full benefits of such a proxy. Every detail from protocol selection, the level of encryption, and configuration defines how well privacy and sensitive information will be guarded. In order to understand the primary functions of them, this article will explain: what is mobile proxy and help users delve into the topic.
Proxies from mobile carriers capture user Internet traffic and forward it through the mobile approach. Proxy mobile IP addresses are employed to receive user requests before sending them out to the web. This makes it possible to perform network activity privately and avoid geo-blocks and restrictions. Unlike all other, mobile proxy types are popular for offering vast pools of rotating IPs which are reliable and don't permit easy identification and blocking.
Mobile proxies have their benefits. They include:
Because of this, these proxies can be viewed as the most appropriate method for dealing with sensitive work on sites that have very tight security.
Mobile proxies are distinct in nature from other types because they are given out by mobile service providers. So, let’s look at how mobile proxies compare to data center, ISP and Residential ones.
To shed light on the principal criteria, we will study the key differences of mobile proxy servers by comparing them on the main criteria.
The source of IP addresses:
Dynamic IP update:
Trust-factor:
IP address sales model:
To better understand mobile proxy features, let us examine their distinctive features compared with other types in the table below.
| Criterion | IPv4 | IPv6 | ISP | Mobile | Residential |
|---|---|---|---|---|---|
| Price | Low, $0.7 each | Lowest, from $0.07 each | Medium, from $1 each | High, from $14 each | High, from $1.5 per GB |
| Trust factor | Below average | Average | High | Highest | High |
| IP rotation | No | No | No | Yes | Yes |
| Obtaining method | Data center | Data center | Internet provider | Mobile network operator | Real users |
| Sales model | Individually/bundles | Individually/bundles | Individually/bundles | Individually | Traffic in GB |
Taking into account the characteristics of rotating mobile proxies, the most common use cases to which these proxies are applied are:
It is conclusive from the comparison above that mobile proxies rank higher than all the other types on several parameters ranging from origin to the cost involved to use them. Such factors determine for which purposes the use of such proxies would be the most effective. They are used primarily by traffic arbitrageurs, SMM professionals, and application developers.
The features determine the productivity, the operational proficiency of mobile proxies and their applicability in various work situations. Let’s analyze the most crucial elements of their functions and see which ones require our advanced scrutiny.
The privacy level is influenced by the type of server. The speed of a mobile proxy connection and the availability of certain resources is also determined by it. The assignment of IP addresses and the specifics of their rotation also determine other factors such as anonymity and restrictions circumvention. And the coverage areas and connection speed are defined by the supported mobile networks (3G, 4G, 5G). The availability of IP addresses in the pool determines anonymity, and restrictions circumvention, the area of use of specific mobile proxies determine scalability, and the number of accounts that can be controlled simultaneously. These factors are further expounded below.
In order to explain the core models of mobile proxy distribution, let us classify based on other previously established types. They can be shared or dedicated, the latter classification stratum has a direct effect on the effectiveness and efficiency of the mobile proxies.
For small tasks and with a limited budget, the Shared option serves as an optimal solution. Dedicated, on the other hand, are perfect for traffic arbitraging, parsing, and social media management because they are efficient and dependable enough for these tasks.
One critical point of consideration when selecting an anonymization service is the details of the IP address, as it defines what the user will be capable of with the mobile proxy server. In this category, some particular details can be noted.
The frequent alteration of dynamic IP addresses makes the processes of tracking and blocking incredibly difficult. Furthermore, there are mobile IP addresses which are kept for some time, known as retained mobile IP addresses. They are more trustworthy than static data center IPs because they are still associated with real mobile devices. Plus, with mobile operators constantly increasing their infrastructure, the additional new IP addresses that supply near endless resources for them are guaranteed to appear.
The pool is a set of thousands of deployable cellular device IP addresses. A gateway server serves as a connecting point by linking to the IP addresses and enabling them to rotate. Upon purchase, the client is provided with the IP address of the gateway server.
IP geo-targeting to artificially conceal the origin of requests and bypass geo-blocks can be made possible by the homeland distribution of the remote IP pool. Connections are more accurate and reliable with a larger pool because they are framed and more diverse.
With rotation, one has the option to connect to a different IP at scheduled times. There are two main types of rotation:
Using all of these advantages, providers are able to give a robust solution of such proxies which automates multi-accounting, scaling online projects, and secures user networks at the same time.
As much as particular categories of mobile networks can be used with proxies, it is a matter of scrutinizing the range of services offered with each category. Provided that, most of the mobile services have a wide coverage from 3G to 5G and their specifics include the following:
When prioritizing proxies that require maximum speed with little latency, 5G is the obvious choice. However, when a stable connection and the ability to easily switch location is more important, proxies based on 4G technology are better choices.
Merely knowing the meaning of: what is mobile proxy not enough for effective usage, a user requires a proper understanding of what one is. This is because the set up is different based on the type of task at hand. This requires one to choose the proper configuration that includes but is not limited to:
For basic surfing the internet, primary settings should be adopted with preference for speed and stability during connection. Multi-accounting requires frequent IP changes to avoid blockage of accounts. Restrictions are bypassed by selection of the countries that do not have limited access to the blocked sites. For security, protocols that encrypt data and change IP addresses regularly are used.
If one would like to surf the web in the most secure, anonymous way while using a mobile proxy for phone or any other device, it would be best to follow the guidelines below:
These factors combined should be enough to provide protection while surfing online.
When it comes to effective resource management, be it e-commerce, traffic arbitrage or just marketing on social platforms, mobile proxies are crucial in ensuring blocks are avoided when working with several accounts at a go.
Multi-account proxy mobile IP settings involve a set of measures directed towards achieving a distinctive fingerprint of each account.
Key elements of such settings include:
Mobile proxy is a vital component in successful multi-accounting because it gives a high level of anonymity by concealing the user’s real IP address and relocating each account to different geographic areas. These features allow the lifting of restrictions that come with having multiple accounts under a single IP address, enhance operational stability, and reduce the likelihood of mass account suspensions/blocking because of increased security.
The first step is to choose the right provider, among whose services it is necessary to pay attention to such factors as:
Each user and his projects have unique requirements. Therefore, the choice between price and performance has to be balanced out in the most optimal way. Also, consider the vendor’s reputation and what other users have to say about it.
In a high quality network, data transfer is rapid, stable, and has low ping. It is also important for mobile proxy providers to work with top cellular operators that have broad coverage and high speed.
In terms of signal quality, region, and the capability offered by the network operator are two essential elements that greatly impact it. It is imperative to understand that 4G and 5G possess the most advantageous features. Modern SIM cards supporting eSIM and antennas with MIMO technology provide a more stable and fast connection. In addition, the load on the network in the selected region should be considered, as this directly affects the speed and ping.
This is critical for people interested in pursuing long term objectives. Primarily, the guarantees from the provider in terms of uptime also need to be properly addressed. Uptime is defined as the duration during which service operates without any troubles, as well as the ability to within short time frames restore the service if something goes wrong.
Improper proxies with these attributes diminish the chances of success by causing data losses and failures, which could severely affect finances. Connection speed is another vital factor that should not be neglected. Proxies that connect faster are able to deliver better results when it comes to executing multiple tasks. Faster connections translate, in most cases, that there is no need to wait and helps with optimizing productivity.
Setting up a mobile proxy is no different for other types, save for one major difference: the user has the option to rotate the IP address on request. It is important to mention, however, that mobile proxy servers are not useful on all types of devices. Rotational mobile proxies for the phone, for instance, do work but are infrequently used. The reasons are quite simple - these ones are more efficient with large scale online projects and demanding software. Here, we will not consider how to set proxy on mobile devices as rotating proxies are more useful on personal computers, together with any needed software.
To configure the set up for the entire Windows operating system, simply do the following:
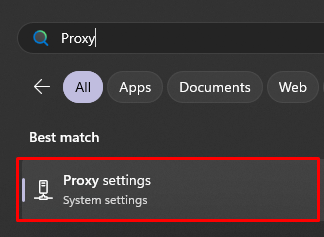
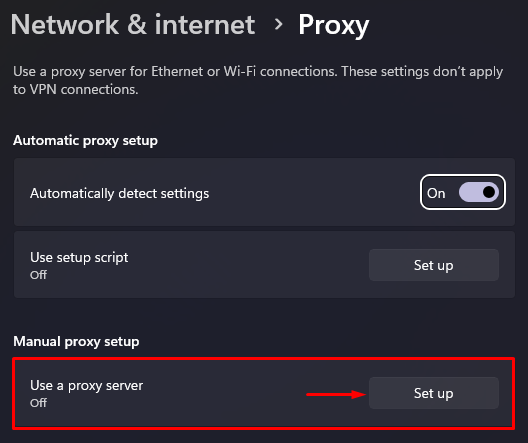
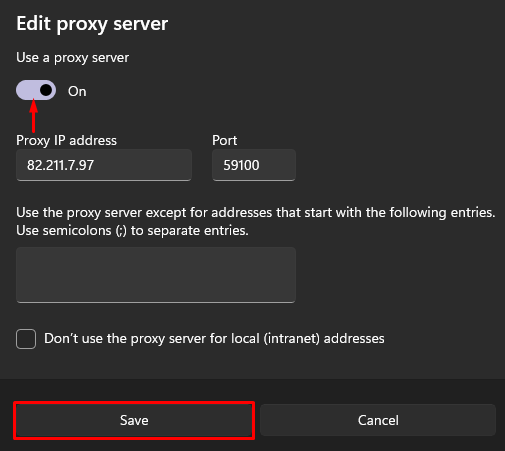
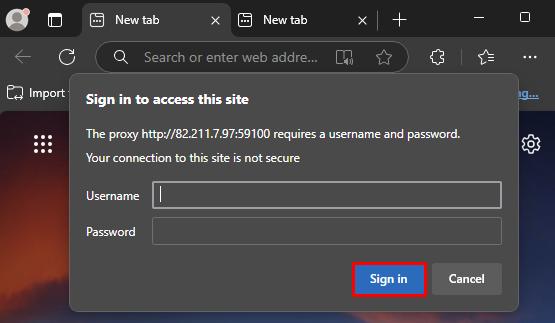
We have examined how mobile proxy works with rotation on request in the Windows OS environment. In cases of time based rotation, there is no need for further steps to be taken after login and password has been saved in the authorization window.
Anti-detect browsers allow customers to leave the right to customize specific fingerprints to each newly created profile and mobile proxies allocate dynamic IP addresses. The combination of those two tools makes it possible to create and control a great number of accounts with no restrictions whatsoever.
As an example, we offer detailed instructions on how to configure mobile proxies in the popular anti-detect browser, Undetectable.
They offer numerous advantages, however, users do run into issues. Some such issues include limitations and blocks on traffic. Arguably, this impacts the user’s connection speed. Moreover, connection instability occurs due to many reasons, including the quality of the mobile network or overloads on the server.
Next, we will examine these issues in greater detail and provide possible solutions. However, the possibility of any issues occurring is minimal.
An area of major concern when utilizing mobile proxies is the inability to surpass a certain speed and volume of traffic. However, some limits can be avoided if a proper provider and tariff plan is selected.
Potential limitations and their consequences:
Users are likely to face minimal limitations because most providers utilizing mobile proxies work through 4G and 5G networks and offer services through tariff plans with good coverage and ship limits on speed. Pair with that the fact that most modern providers practice traffic optimization and compression techniques, leading to reduced network load and increased speed.
The right provider can be selected without running into speed and traffic constraints by following the criteria provided above. Additionally the mobile proxy server can be configured in a way to minimize the traffic used, achieving the greatest level of saturation whilst keeping the restrictions at a minimum.
Mobile proxies are not vulnerable to blocks, unlike static data center ones that have a significantly higher chance of being blocked.They do have some measures to ensure that there are lesser chances of blocks, but do not eliminate them completely.
Consider the potential reasons for blocking IP addresses and the risks to mobile proxy security:
The best way to address these challenges is to use dedicated mobile proxies. This kind of proxy provides the highest level of protection while minimizing the chance of being blocked significantly. A useful tip would be, when a user has to use multiple accounts, one should refrain from creating too many accounts using a single IP address at the same time. Also a coordinated approach to using anti-detect browsers with proxies allows for unique fingerprints to be made for every single account allowing them to keep identification undetected.
This article has explained: what is mobile proxy and why it is regarded as one of the prime solutions for safe online activities as well as project development. Verification of knowledge about the functioning of a mobile proxy, alongside proper settings adjustment for personal needs allows for scaling of activities in the spheres of online data collection, arbitrate buying and selling, data analytics, advertising campaigns launching, or multi-accounting activities.
With help of such proxies, users can bypass local restrictions and access blocked content and websites, secure their personal information from fraudulent users as well as spying by other users. When selecting these services, it is also important to take into consideration aspects such as the speed and stability of the connection, the availability of numerous IP addresses, and the rotation type. In conclusion, mobile proxies seem to be a favorable solution for users targeting high returns on their online work and simultaneously enhancing their security and concealing their identity.
