IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 23 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 14 countries to choose from, rental period from 2 days.
Resident
From $0.90 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:

Handling multiple accounts on social media, marketing platforms, and other online services often involves the risk of account blocking. Anti-detect browsers solve this problem by allowing the creation of isolated profiles, each with a unique digwital fingerprint. Identory is one of the leaders in anti-detect technology, offering a wide range of tools for secure multi-accounting. This detailed Identory browser review 2025 will help users understand what Identory is and how to set up this software for any use cases.
Identory browser is an automated anti-detect solution that allows users to operate freely on the internet. Novice users do not experience a steep learning curve and are able to set up their first profiles with ease. With its sophisticated automation capabilities, Identory streamlines the tedious process of account management for users. As a result, Identory’s anti-detect capabilities are perfectly suited for marketers, arbitrageurs, and anyone else who has to manage a plethora of social media and other service accounts.
Now, let’s start with the review and consider why choose Identory browser is recommended nowadays.
Identory Browser is an anti-detect app engineered to guarantee anonymity while managing multiple accounts. Firstly, it automatically generates unique digital fingerprints for each profile, enabling users to bypass detection and anti-fraud mechanisms. Additionally, the software provides users with advanced customization options that allow setting geolocation, time zone, and even the device or operating system being emulated. To further mask the users’ identities, Identory also is able to operate with numerous proxy servers. The fundamental principle of this app is the creation of an isolated profile, which ensures that data leakage does not occur between accounts.
An anti-detect software is perfect for overcoming advanced anti-fraud systems. Anti-detect multi browsing examples include multi-accounting on betting sites, or getting onto Coinlist. These scenarios require more than just changing IP addresses; there is a need for specific software that can generate digital fingerprints for each account. This allows for account disabling and tracking to be circumvented. Using anti-detect tools like Identory provides users with complete anonymity and safety, a necessity for users handling very sensitive information and a lot of accounts at once.
Identory antidetect allows users network anonymity with various tools at their disposal. A particularly useful tool is the fingerprint generator which creates unique fingerprints for every account. Besides that, the anti-detect allows the creation of an infinite amount of profiles with distinctive unique parameters.
In addition, the app comes with an integrated API for other tools and task automation. The creation of new environments is made easier with the use of preconfigured profiles for different platforms and devices. To shield user information even further, this app comes with script blockers.
Combining all this, users benefit from a high level of security and anonymity, which reduces the possibilities of blocks and data leaks when working with multiple online accounts.
Identory browser features is easy to use and protects users’ privacy thanks to the integrated over one million real digital configurations that allow masks of device fingerprints to be accurately modeled and successfully used to bypass anti-fraud systems. For users’ confidentiality, all such information is only stored on users’ devices. Also, the possibility of running and authorizing through the TOR network adds to anonymity.
Other important features of the Identory include:
In this manner, Identity browser settings simplifies the process multitudes and performs to a high standard making it a popular tool for multi-accounting and digital marketing professionals.
The software implements a set of measures aimed at the user’s protection from phishing, tracking, and sensitive information leakage. One of the most important elements Identory browser privacy because the data is locally stored on the user’s device meaning no third party can gain access or transfer information. This tool does not gather data about the users, hence highly private.
In order to block tracking and phishing of accounts, Identory implements:
Identory browser's advantages lie in the combination of advanced security technology which allows reliable protection from phishing, tracking and data leaks, making it a good solution for safe and private online surfing.
Identory is, indeed, highly efficient in scenarios that require simultaneous usage of multiple active online accounts and automation of processes.
Let's consider a couple of scenarios:
With its rapid adaptability to various usage scenarios, Identory guarantees stable, fast operation, making it a proficient solution for experts managing multi-accounts or requiring high performance from their software.
In the next blocks we provide a demonstration of how to use Identory through the anti-detect feature’s breakdown within the features overview as well as the how to set up Identory browser profile for the initial use of the application.
This part of Identory overview contains important parts of the description of the anti-detect system and will enable the user to get acquainted with the main features and their functions.
At the “Profiles” tab, users can work with new and existing accounts along with corresponding parameters, which include digital fingerprints, proxies, and multi-accounting environment. In this part, users have the ability to sort, filter, and search profiles which makes management easier. Users have the ability to group it, add comments, and set statuses which is very helpful in data-rich environments and collaboration among teams.
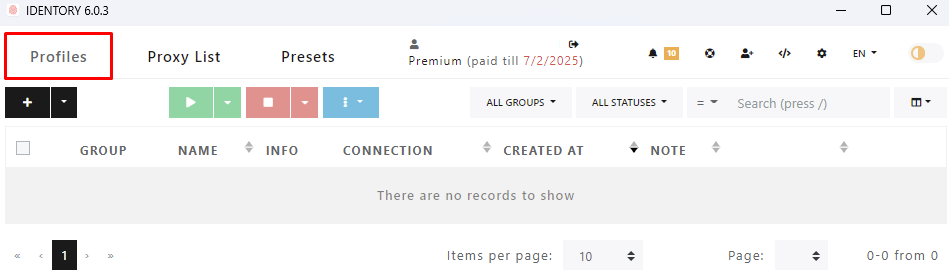
This tab serves for adding, viewing, editing, organizing, and assigning proxies to different accounts. Proxy servers can be filtered and sorted by their statuses, providers, and other parameters. Additionally, there are mass change operations, connectivity tests, and IP swaps, which help in managing numerous connections more easily.
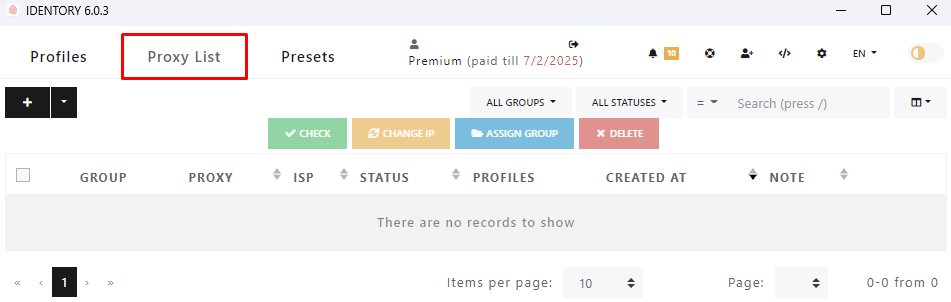
Users can create and manage environment presets that are pre-configured in the system using these features. Presets apply previously configured parameters such as proxy and digital fingerprint, headers, and other identity attributes. Users have permission to create, import, export, and erase presets and use them to create new profiles without manual configuration which is, indeed, a very useful feature.
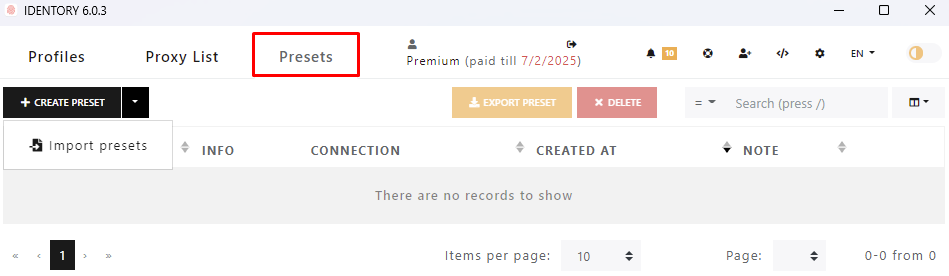
You are now able to manage the browser programmatically, create scripts for automating various processes, and integrate other systems using the API. This is where the API comes in. It transforms Identory from a simple browsing tool into an automation and development platform. Developers working with the API can find detailed documentation for using the API.
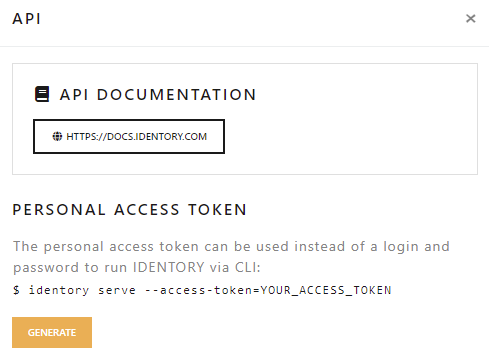
The settings within the Identory antidetect gives users complete flexibility in managing automation tools and protection measures. With these options, users can complete a wide variety of tasks in the most comfortable way, with the ability to modify workspaces and set IP names for simple identification. Users can easily control remote sessions, and for teams managing several accounts, this feature highly increases organization. The anti-detect browser settings enable management of all parameters of web activity.
Finally, another interesting fact about Identory. For the comfort and needs of every individual user, it offers the ability to customize the language of the interface, as well as the lighting theme which can be set to either dark or light. With so much ease in customizing the browser, every single user has the ability to tailor their work environment even further.
After learning how to set up the Identory browser and its features, let's create a profile that includes setting up a proxy server. Follow the instructions below for seamless execution.

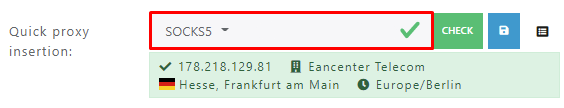
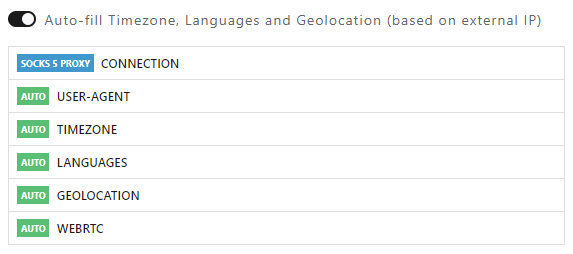
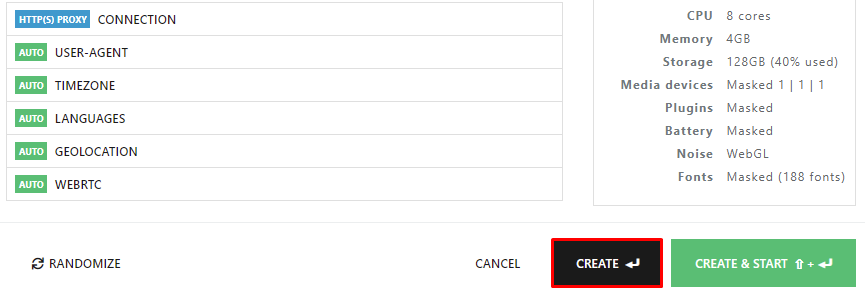
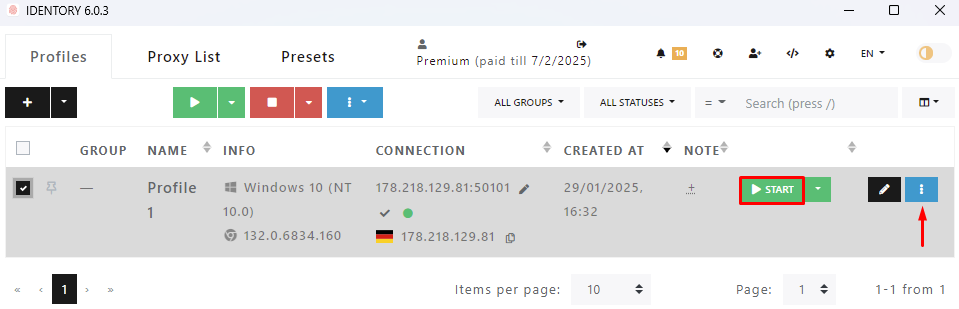
That’s it. The profile is created now and can be further edited and used online. In addition, when creating a profile, one can use advanced settings such as importing cookie files, hardware settings, bookmarks, and extensions.
In this part, we discuss this tool, its prerequisites, and scope of application, as well as how this program ensures privacy for users working with many projects on the web.
Identory is a particular web-tool designed to serve specific purposes that offers unique and specialized functions as mentioned below:
As such, Identory makes it possible to control multi-accounts on social networks, marketing services, and other web resources without the risk of exposing personal data. Users seeking for an online solution that provides automation within confidentiality while scaling projects and campaigns will find this app most suitable.
Identory’s primary function is to assist users in staying private and anonymous while surfing the web. Nonetheless, the technology has its strengths and weaknesses. Now, we will discuss the advantages, as well as disadvantages, if any.
Amongst other Identory browser features, perhaps the most important one is, the degree of privacy offered by the substitution of digital fingerprints and working with the TOR network. The browser has in its possession over a million real fingerprints which makes it very popular for bypassing anti-fraud systems. Completely local data storage increases security by eliminating the chances of leaks through cloud services. It can also be used for multi-accounting, traffic arbitrage and SMM because it stably operates even with hundreds of profiles being launched.
Tools for managing proxies allow control over geographical profile features. Puppeteer, Playwright, and CDP integration enables automation convenience. Modern tracking circumvention tactics are achieved through system updates to the fingerprint substitution and Chromium core along with an user-friendly interface to manage profiles, even for novices.
There are some limitations with the app despite the many benefits it has. Firstly, it needs fairly powerful hardware to manage a large number of profiles, as it might use significant RAM and processor resources. Secondly, the tool has fewer built-in options for collaboration than competitors which may affect use by larger businesses. Thirdly, there are no free or trial versions available and all paid options are subscription-based.
Even with reliable network protection, the browser does not guarantee reliable access to all anti-fraud systems, especially if low quality proxy servers or poorly configured profiles are used. Still, for most activities requiring safe online work, multi-accounting and other, Identory is a reliable solution.
To sum up, the Identory browser offers the most advanced digital fingerprint masking technologies, stable performance, and high confidentiality. The use of anti-detect is a priority for professionals working with advertising cabinets, marketplaces and social media where bypassing anti-fraud systems is essential. Users are granted maximum control over anonymity thanks to local data storages and advanced IP configurations.
Identory remains one of the most popular anti-detect browsers despite requiring some technical device resources and detail oriented configurations. It serves the purpose of both advanced users and novices who wish to ensure security and privacy while conducting activities online. Its stability, high frequency of updates, usage of automation, and support make it an exceptional anti-tracker solution for clients that seek to reduce the chances of being tracked or having their data leaked.
