IPv4
From $0.70 for 1 pc. 40 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 40 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 40 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 21 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 14 countries to choose from, rental period from 2 days.
Resident
From $0.90 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
Checking open ports on an IP address or a website is crucial for understanding network security and functionality. Here are some effective methods to perform this task:
While the choice of method may depend on your level of experience and preference, using online scanners is generally the quickest and most straightforward option for most users. These scanners require no special knowledge and deliver the detailed information needed for thorough analysis.
IP ports are numeric identifiers that locate specific applications or processes that need to connect over a network. They are essential in the TCP/IP model, ensuring that data is sent to the correct service. Each network service or application generally operates on a designated port to facilitate its specific functions.
Key functions of Internet ports:
Ranges and types of internet ports:
Examples of commonly used ports:
These ports are widely used by services and applications to pinpoint specific processes and establish connections.
Although there are many ports, those in the range of 0 to 1023 are termed “privileged” ports. These privileged ports, reserved primarily for network services, are crucial for the efficient routing of data across a network. They ensure that devices accurately relay information to the intended application.
A port scanner is a program or tool used to examine network ports on devices within a computer network. It is designed to detect open ports on remote hosts, identify active services and applications, and evaluate network configurations for potential security vulnerabilities.
The operation of a port scanner varies based on its type and functionality. The process of port scanning includes the following steps:
The main purposes of using a port scanner include:
Port scanner functionality allows for the examination of TCP ports, which are used for secure data transfer, and UDP ports, which are intended for rapid data transmission.
Analyzing Internet ports helps gauge how well a user's device is protected against potential attacks and data breaches. Importantly, scanning does not necessitate the installation of specialized software or extensions. Customers can simply utilize our tool, “Port Scanner” which is built on nmap. This tool offers a quick and free way to check for open ports on the target host, providing vital information about the ports available for establishing connections.
To begin scanning, follow these steps:
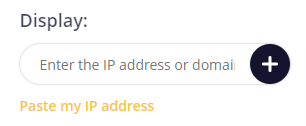
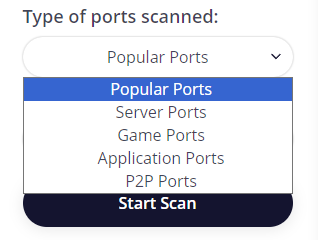
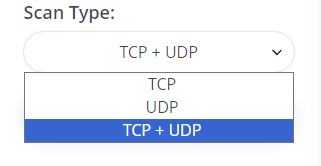
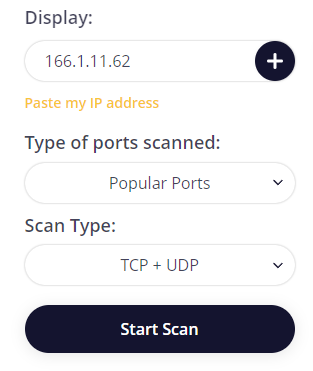
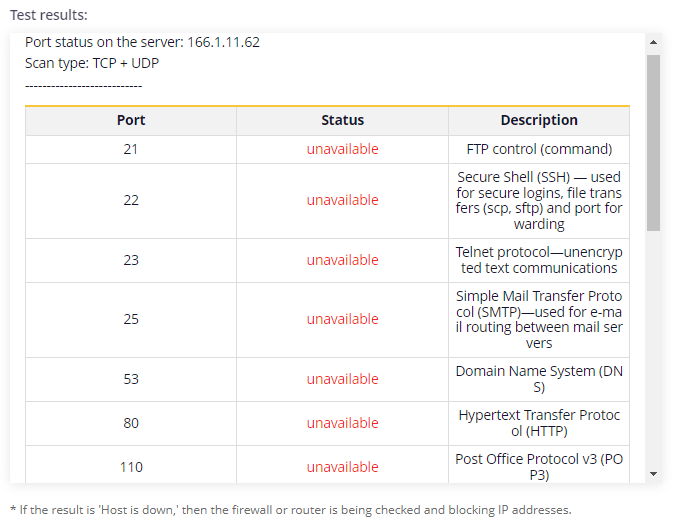
Once the scan is complete, users can analyze the information for each port of the IP address or website. This analysis can help improve the network's security level and enhance interaction with web resources.
