IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 23 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 14 countries to choose from, rental period from 2 days.
Resident
From $0.90 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
Botnets alongside AI algorithms are increasingly used to organize DDoS attacks, making them more powerful and resistant to countermeasures. Companies operating in the fields of finance, online gaming, and cloud services, require advanced security measures such as anti DDoS proxy, which filter suspicious traffic and can ensure stable operation even under intense loads.
Here, we will focus on all aspects concerning proxy for DDoS prevention used, their relevance in combating harmful attempts, the optimal types of proxies available, as well as how to bolster the security of the systems within the organization.
A DDoS attack is defined as a form of cyberattack which renders online services inaccessible. The attack is executed via a botnet, which is a network consisting of servers, Internet of Things (IoT) devices and hacked computers controlled by malicious actors.
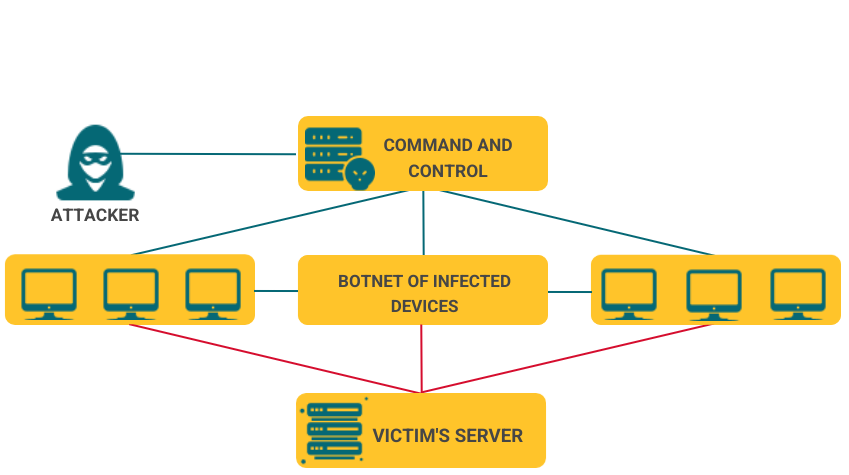
They make use of overwhelming the server compute power by sending an abnormally large number of requests or constraining the bandwidth available for data transfer in the network.
There could be various reasons for conducting such attacks which include:
To understand how it disables services, it is important to comprehend which levels of the network resources they aim at. Here, the OSI model explains the division – in seven stages – of how data transmitting takes place in the network, elaborately fulfilling each stage with precision.
Every level has a set of responsibilities assigned while working. The table below shows what types of attacks exist and how they operate.
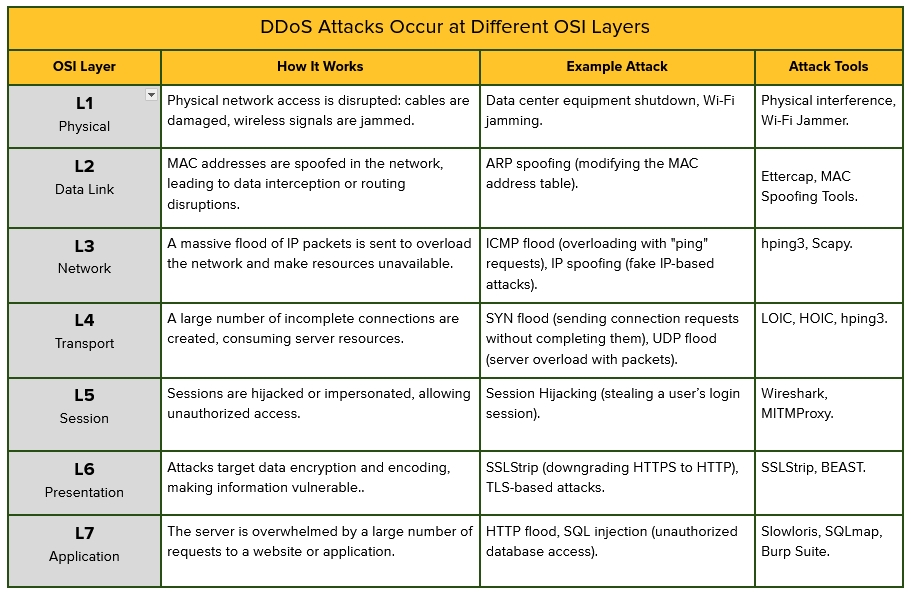
The most common methods include:
They cause massive reputational and financial damage to companies and users such as:
In 2022 Google suffered a load attack of DDoS at an astounding magnitude of 46 million requests per second. If the attack was not mitigated the company's operational downtime may have cost the company nearly half a million dollars with the loss potentially reaching to multi million per day. This is a clear example of why building a proficient protection is key. In the next block, we will analyze one of the highly sought after tools used for this purpose.
Proxy server helps in DDoS attack prevention, because of such reasons:
These mechanisms significantly limit the chances of a successful attack, placing an additional barrier between the attacking source and the intended system. Let us now observe how an anti DDoS proxy can mitigate the risks of attacks.
The strategic allocation of load across various nodes is crucial in the case of DDoS attacks that produce a disproportionately high volume of requests, likely to surpass the limits of a singular server.
How it works:
Why load balancing via proxies is advantageous:
Specific IP addresses that belong to company servers are normally the main target. If the attackers are aware of these pieces of information, they will readily be able to confront protective server measures.
Proxies prevent this by masking the IP address of the infrastructure. As a result, users are able to interact through the intermediary server, which appears as follows:
Consequently, the attacker only has access to the proxy server's IP address without any knowledge of the actual location of the protected resource.
Proxies serve a dual purpose: they transmit data while simultaneously monitoring requests for any potentially malicious traffic, which they can block if necessary. This helps mitigate the effects of such traffic even before they reach the boundary of the protected servers.
How protection using proxies against DDoS is achieved through filtering:
That’s how proxies stop DDoS. Servers are less impacted because, during the proxy stage, harmful requests are already eliminated. This also aids the automated removal of bots, which helps safeguard resources from manipulation, spam, and automated exploits. Users can also benefit from being able to tailor the configuration according to their needs and the severity of the threat.
DDoS protection proxies are indeed effective, but not all types are equally effective in different situations. Reverse and transparent proxy servers are most commonly used for those kinds of purposes.
Both types relate to prevention of violations different in manner:
Let's take a closer look at how they function and the corresponding case scenarios in which they are applicable.
This type operates by forwarding user requests to a target server which is situated behind it.
How a reverse proxy protects anti DDoS attacks:
This strategy is meant for safeguarding API services, websites, and corporate networks to withstand abuses and overloads. It is an added layer for web apps and sites to defend servers from being affected. For the case of API services and protection from DDoS, reverse proxy are preferable options.
This type is a part of the network at the level of the provider, router, or corporate server and operates without any modification to the original request. They seldom mask the IP address, meaning they are frequently paired with other more complex methods like network filters and security gateways. However, the application of these anti DDos proxy type is more complex than that:
Additionally, proxies in public Wi-Fi connections, like those available in cafes and airports, survey the level of connection security, check for the reach of unsafe sites, and control traffic on forbidden materials. For providers, this is simply an instrument that shields the clients from dangerous resources and inhibits the risk of cyber-attacks.
Here are a few tips for choosing the best DDoS proxy protection:
| Proxy type | Operating principle | Application | Advantages |
|---|---|---|---|
| Reverse | Accepts requests from users and redirects them, hiding the real IP address of the target server | Websites, cloud services, API | Directly protects the system from attacks, evenly distributes the load |
| Transparent | Redirects occur without changes and hiding the client or server IP address | Corporate networks, public Wi-Fi, providers | Instantly recognizes potential threats and stops suspicious connections before they can cause harm |
As is the case with many resources, it is best to use reverse ones for user protection. For more general security measures transparent type can be used.
As a safeguard for such activities, proxies should be guaranteed the best results whenever possible. With the help of a reliable action plan and the accurate configuration of proxies, desired outcomes can be met.
After implementing the proxy server, there are other conditions that should be considered to enhance the server’s protection by avoiding an attack:
If dynamically adjusted proxies are established alongside security practices, the chances of facilitating DDoS attacks are dimmed a lot while mitigating the chances of diversions having an impact on system reliability.
In a world where the frequency of attacks increases, the role of proxy DDoS protection becomes more significant in terms of cybersecurity in safeguarding infrastructure and defending assets of utmost priority for maximized availability.
Proxies are only one aspect of many other protective measures that need to be instituted in order for security to be at the pinnacle of performance. For example, geo-filtering access can be limited from certain suspicious areas and request volume limits can also help mitigate irregular actions, while constant observing of the traffic enables timely response for threats.
