IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv4
From $0.70 for 1 pc. 41 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 23 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 14 countries to choose from, rental period from 2 days.
Resident
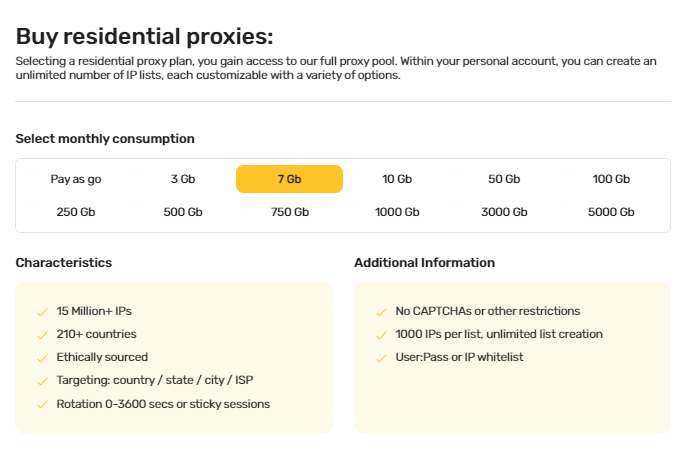
From $0.90 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
Proxy servers play a critical role in online anonymity, automation, and data access. There are four main types of them: datacenter, residential, mobile, and ISP. Among the mentioned types, residential ones tend to capture more attention because of their versatility and dependability. In this article we are going to explore what is a residential proxy and other features alongside as well as how to purchase them and create a new list.
So, let’s start with the: what is residential IP? Such IP addresses possess a high level of trust since they come from real home networks all over the world. They, unlike data center ones, are registered with a valid ISP; therefore, they are less likely to raise the suspicion of web service security systems. Moreover, the broad geographical coverage of these servers makes it possible to access regionally restricted content or resources.
Now, when we know residential proxies meaning we can proceed to their way of obtaining as it differs from those of data centers. Data center IP addresses are derived from servers located in data centers, and residential ones are sourced from real people who lease or rent out their IP addresses.
Obtaining them can be divided into two methods:
This approach consists of renting access from users who have provided consent through some form of user agreements. Our organization enters and maintains rental agreements because we have contracts with device or application owners who provide access to their traffic in exchange for a payment. The payment could be in the form of a bonus, a premium subscription or other services. The dedicated residential proxies are willingly offered based on voluntary consent from users. Consent is typically obtained through the installation of an application, website, or browser extension that distributes traffic.
Trying to obtain residential proxies without user's consent leads to illegal sudden obstruction of power, unlawfully gaining access to an individual or organizations secure networks through malicious means such as hacking which is unethical. This could include the use of botnets, malware, or other methods to commandeer users' devices against their will. IPs are harvested without permission from the owners and the owners of such information. Apart from legal provisions within laws such actions breach there is also secure breach to owners of controlling devices.
Such practices can expose users to various risks:
It is possible to incur reputation damage, fines, and account or IP bans when using such proxies sourced without permission. Trustworthy providers do exist, and servers must be sourced from them as they ensure ethical procurement of IPs which grants use of a safe network.
Ethically sourced private residential proxy operates differently compared to server one. In this case, the clients purchase MBs from a provider who gives access to a pool of IPs belonging to actual users. The IPs are loaded onto the client’s software, allowing secure protected connections to data and interception leakage. Users can evade geo-restrictions or blocks on certain websites.
The capability of such servers to deliver geolocation IPs from nearly any part of the globe, even as precise as the region, city, and Internet service provider level, is a remarkable benefit. This is made possible because user IP addresses are provided in large swaths, and users’ traffic is distributed during online sessions. When a user who provides access to the IP ends their session or logs out, another IP of the same locale is provided.
It is worth noting that the traffic from residential proxy networks is more costly than that of ones from data centers. Purchase of them makes sense for certain use cases, like web scraping when data gathering is done. They improve the reliability and the control optimizations balance performance with responsiveness the driver and web sites interact with, enhances anonymity, and reduces blocking risks. Many web resources impose limits on the number of requests permitted from one IP address in a given timeframe. Regularly changing IPs enables the scraper to circumvent having their requests restricted. Such a server will intelligently connect to the sites using geographically dispersed IPs located in various locales to prevent captcha and erroneous response issues during the scraping process.
Based on the method of rotation and sales model, they can be subdivided as follows:
Types of rotation:
Sales models:
The selection is based on the requirements of the user’s project. Dedicated servers are usually recommended as they are used exclusively by a lone individual and permit the selection of sticky or rotating rotation types based on the requirements of the designated task.
Their uses range from e-commerce price monitoring, ad tech verification, ad fraud detection, to even enabling travel platforms to check for dynamic pricing. Businesses also use them to test personalized content and region specific launches.
Different tasks can vary greatly in terms of data usage, especially when it comes to the number of requests and the size of transferred content. The most accurate way to assess actual consumption is through hands-on testing, which is why many providers offer trial packages. These allow users to estimate usage requirements based on their specific workflows, such as monitoring or scraping activities.
The table below provides an approximate baseline for minimum data needs across various project types. This represents a rough calculation.
| Task | Ranges of minimal traffic consumption |
|---|---|
| Web-scraping | From 10 kilobytes to several megabytes per page, depending on its size, the number of images, and other multimedia elements. |
| API requests | From a few kilobytes to several tens of megabytes, depending on the complexity of the request, the volume of data returned by the API, and the response format, such as JSON or XML. |
| Social media | Varies from a few kilobytes to several tens of megabytes depending on the type of interaction, such as posting, uploading images, downloading content, and the type of platform. |
| Watching video | Uploading a video consumes a large amount of data, ranging from several tens of megabytes to several gigabytes, depending on the video quality and duration. |
| Bypassing blocks and geographical restrictions | A small amount of data, often less than 1 megabyte, as the main goal is to provide access to blocked resources. |
| Testing API and web applications | From a few kilobytes to several tens of megabytes depending on the number and complexity of requests, as well as the amount of data transmitted in each request. |
When you opt in for the trial package on our website, you pay a fee and then receive 200MB to be used within a 3 day period. This is a great way for people to gauge the consumption of residential proxies relative to how they work before fully committing to the pricing plan.
For further details about our pricing plans, refer to the “Residential proxies” section of our website.
Now, let’s explore how to make residential proxies list properly with this step-by-step guide below:
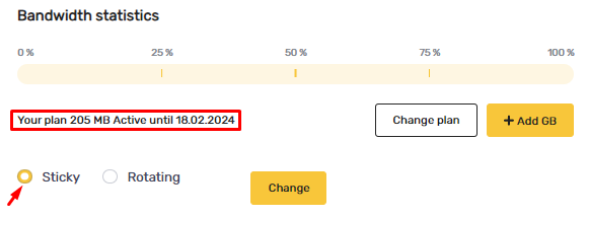
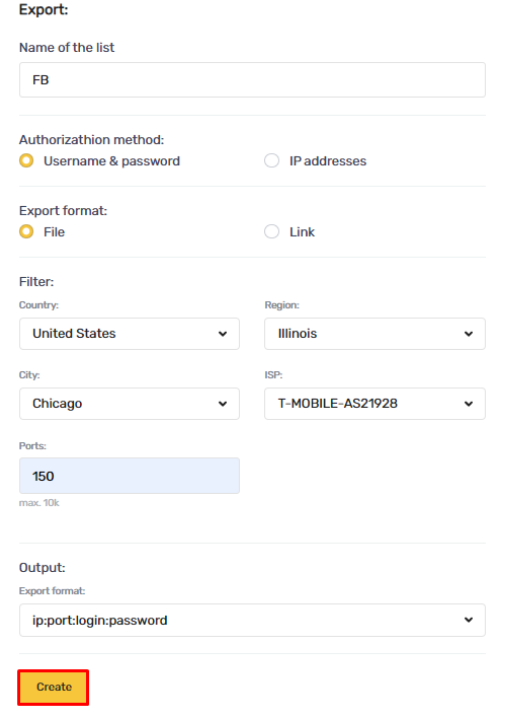
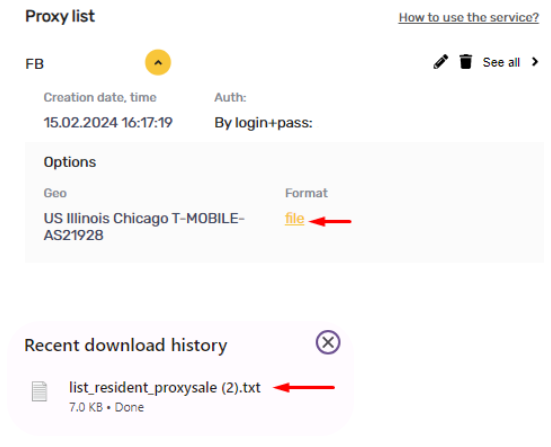
All IPs in the file will use the same gateway server. After walking through the configuration steps, the actual IP address will be disclosed. This can be verified utilizing our free service, “My IP”.
Now, we know how to use residential proxies. Their trusted IPs from providers and hosts are valid. As an added bonus, servers of this type are present in a myriad of regions and countries. This allows users to access geo-restricted content outside of their regions.
The versatility of such a type excels the users in their tasks like profile promotion, automation of processes, multi-accounting, website scraping, and data analysis. Users can also set the rotation and authorization type, and supervise MBs consumption allowing smoother project execution.
It depends on the tasks at hand. If you want to manage social media accounts or log into user profiles, static ones will best suit you since these tasks require stable identity throughout the session. However, if your work has tasks like scraping a lot of data or monitoring prices, then rotating options work best since they frequent IP changes that evade detection.
Yes, as a matter of fact, they do assist in avoiding CAPTCHA measures. Because real IPs provided are used, it is more difficult for CAPTCHA systems to detect them, hence making them more effective. Additionally, the use of rotating servers optimizes the chances of succeeding CAPTCHA bypass as the chances of facing rate limiting as well as bot detection are lower.
The exact number of IP addresses depends on the selected location and provider. You’ll get access to a pool of addresses available within the parameters you’ve chosen.
