Checking open ports on an IP address or a website is crucial for understanding network security and functionality. Here are some effective methods to perform this task:
- Online scanners - these tools are user-friendly and efficient, perfect for quickly scanning open ports on a specific IP address or website. Enter the IP address or domain name, and the scanner will reveal the open ports along with their status, helping you detect any vulnerabilities.
- Command line - this method is available on most operating systems and is particularly useful for those who prefer a hands-on approach. Whether you’re using Unix/Linux or Windows, command-line utilities allow you to check the availability of specific ports on a given IP address.
- Specialized software - for those needing more detailed analysis, specialized programs designed to analyze network traffic and scan ports can provide comprehensive insights. These tools offer advanced features for a deeper dive into network activity.
While the choice of method may depend on your level of experience and preference, using online scanners is generally the quickest and most straightforward option for most users. These scanners require no special knowledge and deliver the detailed information needed for thorough analysis.
What are IP and proxy ports responsible for?
IP ports are numeric identifiers that locate specific applications or processes that need to connect over a network. They are essential in the TCP/IP model, ensuring that data is sent to the correct service. Each network service or application generally operates on a designated port to facilitate its specific functions.
Key functions of Internet ports:
- Traffic routing - ports direct incoming requests to the appropriate application, based on its designated port number.
- Sharing - multiple applications can use a single network connection simultaneously, thanks to ports.
- Security - certain ports are earmarked for essential system services and are integral to security mechanisms like traffic filtering and access control. For instance, network administrators might close off ports or set up firewall rules to block unwanted traffic.
Ranges and types of internet ports:
- 0-1023 - reserved for system services and applications;
- 1024-49151 - typically assigned to user applications: HTTP, FTP ,SSH;
- 49152-65535 - dynamic ports, used temporarily by applications for specific tasks.
Examples of commonly used ports:
- Port 80: Facilitates HTTP traffic, primarily for accessing websites;
- Port 21: Supports FTP for transferring files between systems;
- Port 25: Manages SMTP traffic for sending emails.
These ports are widely used by services and applications to pinpoint specific processes and establish connections.
Although there are many ports, those in the range of 0 to 1023 are termed “privileged” ports. These privileged ports, reserved primarily for network services, are crucial for the efficient routing of data across a network. They ensure that devices accurately relay information to the intended application.
Why use a port scanner
A port scanner is a program or tool used to examine network ports on devices within a computer network. It is designed to detect open ports on remote hosts, identify active services and applications, and evaluate network configurations for potential security vulnerabilities.
The operation of a port scanner varies based on its type and functionality. The process of port scanning includes the following steps:
- Target device selection - the user specifies a target device or a range of devices to be scanned.
- Selecting of a scanning method - various methods are available, including full scanning, targeting specific ports, scanning ranges of ports, or using different protocols such as TCP or UDP.
- Scan initiation - the scanner sends network requests to the target device to check the availability of ports and analyzes the responses.
- Analysis of results - the scanner assesses responses from the target device and determines the status of each scanned port—open, closed, or filtered. An open port indicates that a network service or application is active on that port, a closed port means no service is active, and a filtered port suggests the port is blocked by a firewall or other security measures.
- Result output - the port scanner provides a report of the scan results, detailing information about open ports, the services and applications identified, and other aspects of the device's network configuration.
The main purposes of using a port scanner include:
- Identification of services and applications. Scanning allows you to determine which services and applications are operational on a remote computer or website.
- Detection of vulnerabilities. Open ports may be vulnerable if not associated with legitimate applications. Port scanning helps in identifying potential security weaknesses that could be exploited by attackers.
- Monitoring network changes. This is useful for detecting new devices that have been connected to the network, or changes in the configuration of existing devices.
Port scanner functionality allows for the examination of TCP ports, which are used for secure data transfer, and UDP ports, which are intended for rapid data transmission.
How to use an IP address or domain port scanner
Analyzing Internet ports helps gauge how well a user's device is protected against potential attacks and data breaches. Importantly, scanning does not necessitate the installation of specialized software or extensions. Customers can simply utilize our tool, “Port Scanner” which is built on nmap. This tool offers a quick and free way to check for open ports on the target host, providing vital information about the ports available for establishing connections.
To begin scanning, follow these steps:
- Enter the IP address or domain in the designated field.
- Choose the type of ports you want to scan from the drop-down menu.
- Specify the port type.
- Once all the options are selected, click the “Start Scan” button.
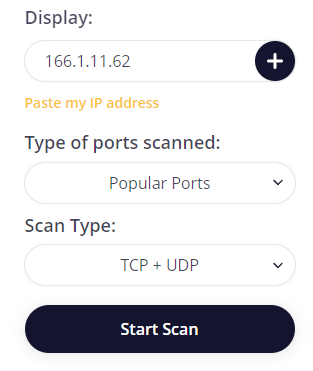
- After a few seconds, the test results will appear in the designated field.
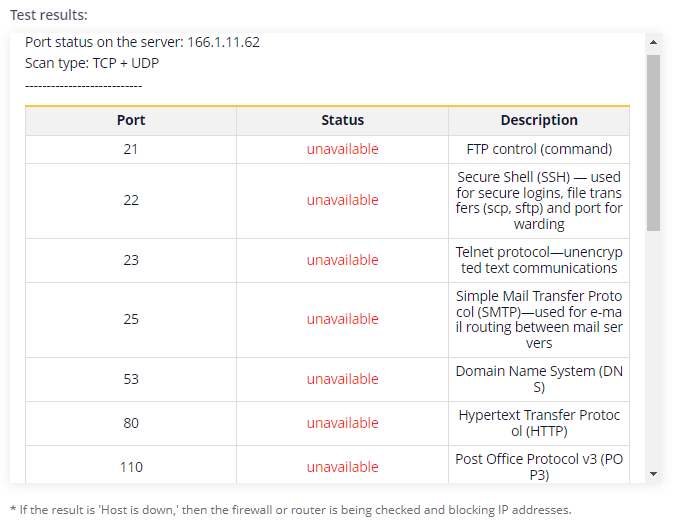
Once the scan is complete, users can analyze the information for each port of the IP address or website. This analysis can help improve the network's security level and enhance interaction with web resources.




